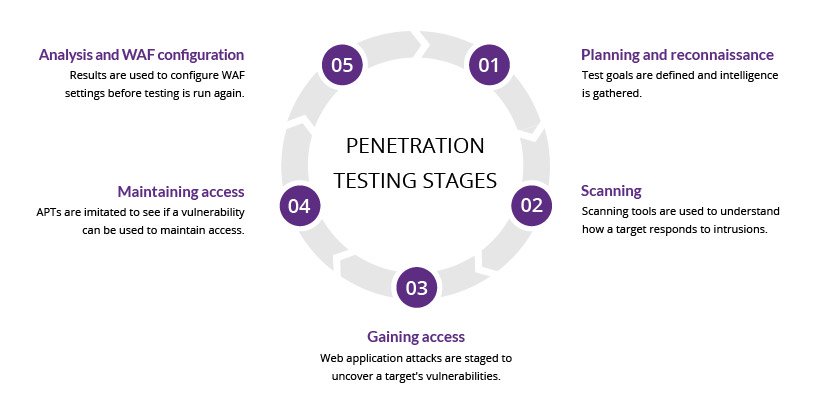
Penetration testing, often referred to as “pen testing,” is a cybersecurity practice that involves simulating real-world cyberattacks on a system, network, or application to identify vulnerabilities and weaknesses. The process typically consists of several phases, which can vary slightly depending on the specific methodology or framework being used. Here are the common phases of penetration testing:
- Preparation:
- Define the scope: Clearly outline what systems, networks, or applications are within the scope of the penetration test. This phase involves setting boundaries and goals for the test.
- Obtain permissions: Ensure that you have the necessary permissions and legal authorization to conduct the penetration test on the target systems.
- Gather information: Collect information about the target, such as IP addresses, network architecture, software versions, and any available documentation.
- Reconnaissance:
- Passive reconnaissance: Collect information about the target without directly interacting with it. This may involve researching publicly available information, social engineering, or using open-source intelligence (OSINT) techniques.
- Active reconnaissance: Probe the target to gather more detailed information, such as identifying open ports, services, and potential vulnerabilities.
- Scanning:
- Port scanning: Use tools to scan for open ports and services on the target system or network.
- Vulnerability scanning: Employ vulnerability scanning tools to identify known vulnerabilities in the target’s software, configurations, or systems.
- Enumeration:
- Enumerate services: Gather additional information about identified services, including version information and configurations.
- User enumeration: Identify valid user accounts and access levels within the target system or application.
- Vulnerability Analysis:
- Analyze the results of the vulnerability scans and manual testing to identify potential weaknesses and vulnerabilities.
- Prioritize vulnerabilities based on their potential impact and likelihood of exploitation.
- Exploitation:
- Attempt to exploit identified vulnerabilities to gain unauthorized access or control over the target system.
- This phase involves ethical hacking techniques to demonstrate the impact of the vulnerabilities.
- Post-Exploitation:
- Maintain access: If successful in gaining access, attempt to maintain control over the target system to gather more information or conduct further attacks.
- Privilege escalation: Try to elevate privileges to gain greater control and access.
- Data exfiltration: Extract sensitive data if it’s within the scope of the test.
- Reporting:
- Document all findings, including vulnerabilities, their impact, and any recommended remediation steps.
- Provide a detailed report to the client or organization that commissioned the penetration test.
- Cleanup and Remediation:
- Ensure that any changes made during the penetration test are rolled back to their original state.
- Assist the client or organization in addressing and remedying the identified vulnerabilities and weaknesses.
- Verification:
- Re-test the previously identified vulnerabilities to verify that they have been adequately addressed and remediated.
- Ensure that the security improvements have been effective.
- Final Reporting:
- Provide a final report to the client or organization, including the results of the verification phase.
- Offer recommendations for ongoing security improvements and best practices.
These phases are iterative and may be revisited as needed to ensure thorough testing and remediation. The goal of penetration testing is to help organizations identify and mitigate security risks before malicious hackers can exploit them.
Some organizations create competing teams to conduct penetration exercises that are longer than a penetration test.
For instance, in such a scenario, there can be three or four teams:

- The red team is the adversary, trying to attack the system while remaining unnoticed.
- The members of the blue team are the defenders and they try to thwart the efforts of the red team.
- The white team is a neutral team that defines the goals and rules and oversees the exercise. Members of the white team are less technical but possess knowledge about governance and compliance. The white team is the referee of this exercise.
- Sometimes, there is also a purple team, where members of the the red and blue team work together to identify vulnerabilities and explore ways to improve controls.