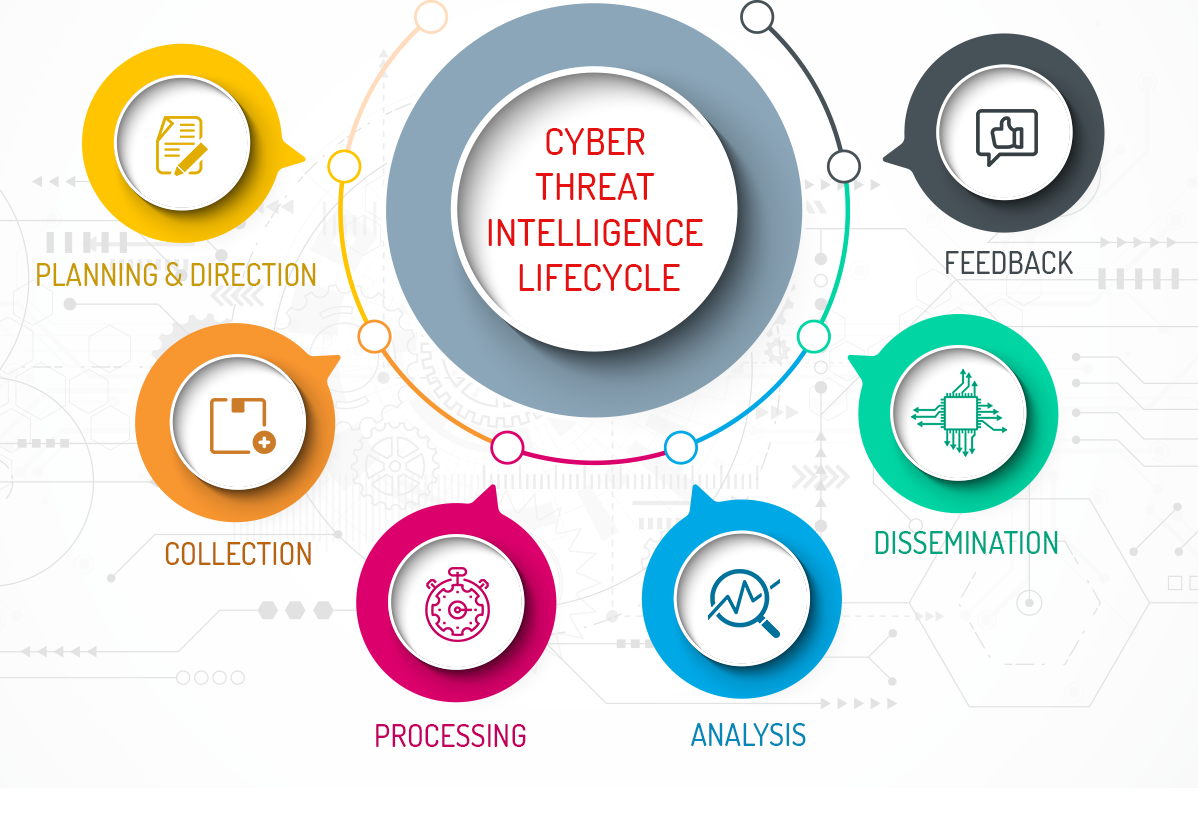
There are different types of attacks. Two of them are non electronic and electronic attacks.

1.Non Electronic Attacks
Someone just looks over your shoulder, or maybe they have binoculars or a telescope and are looking from one office building into another watching you type, or maybe they’re hacking your brain. That’s right. Also, dumpster diving where people throw things away that they don’t consider to be important, but an attacker can use that.
2.Electronic Attacks
There are active online attacks where the attacker does a direct attack using brute force or dictionary techniques. Dictionaries. If you go online and you look for password dictionaries, you can find password dictionaries that are over terabyte in size and this is actually pretty interesting because these are text files, meaning that there are billions and billions of passwords in these text files that can be used for dictionary attacks.
Brute force attacks will take every possible combination. Now, I want to tell you that brute-force attacks are difficult to do because they take an extraordinary amount of two things. Number one, computer resources, and number two, time. When I say an extraordinary amount of time for a brute force attack, I’m talking about enough time that every star in the universe will have evaporated.
In fact, for a long passphrase, it can take more time than you can get in 20 universes. Brute forcing can take a long time, but there’s a technique called caveat. The caveat is those brute force techniques which are using modern computers. There’s a new class of computer that is not just advancing in an exponential fashion but is advancing geometrically. It’s going to sneak up on you.
And that is Quantum computers. let’s say that there are 10 billion items. Rather than just examining one item at a time, a quantum computer examines all items simultaneously, which allows it to do a lot faster. Eventually, you’re going to see quantum computers used in brute-forcing attacks. And the more important is to make sure that you have your authentication ready for the future.
A rule-based attack is one of the rules that make up the password hash injection and it’s wherein we inject a known hash of a password. One of those would be LLMNR/NBT-NS poisoning, where you have a lab that you can try that out. There are Trojans, spyware, key logger, and even guessing the password, which hardly ever works .
There are other types of password attacks including passive online attacks. These are where you are logged into a network or you’re somehow on the network, not necessarily logged in, but you’re able to run a sniffer like Wireshark and do wire sniffing or even run a man-in-the-middle attack,

A replay attack is when you take the information that you’ve discovered through sniffing and you play it back to the resource that the user was using to see if you can get in and now most of these wire sniffing, yeah, you can get a lot of information.
Man-in-the-middle attacks.
Yes, there are many different ways to do those, but replay attacks don’t usually work very well.
Then there are offline attacks where you take the information, takes the list of password hashes,
and then you use pre-computed hashes in rainbow tables. Rainbow tables like a dictionary file,
but it’s just the hashes from the passwords that you would find than a dictionary file. Then you can take those and you can even use a distributed computer program to help speed up the attack or even upload the hashes and run distributed computing in the Cloud, AWS or Azure

I’ve mentioned a few terms and we want to make sure you understand what they are. Number 1, I’ve mentioned Dictionary. For instance, if you go to a tab, go to Google and you do a search and the search would be top 1,000 passwords, or if you want you could do top 100 passwords and you’ll see a list of password, everything from 1, 2, 3, 4, 5, 6, 2, 1, 2, 3, 4, or 5 to 100s, to people’s names, etc. Those are some of the top files that for instance you’d find in a dictionary file, but then you’d also have not just the top 100, not just the top 1,000 but the top 100,000 or the top million or even more. What happens is the dictionary of a commonly used passwords, passphrases, etc., and also compromise passwords will be used against the resource that the attacker is trying to attack.
we also have Brute force attacks I was talking to you about that and the possible future role of quantum computation in brute force attacks. With brute force attacks, what you’re doing is you’re taking every possible combination of characters.
Rule-based attacks, you have some information about the past or so. For instance, let’s say that an employee has an employee badge. The password is the first five digits of the employee number dash some password. If that’s the case, the attacker would say, oh, hey, I know the first part of every password of this organization, so all I have to do is figure out the second part because there is a rule. A rule is some type of information about the password that happens with every password.

Well, the first thing that happens is the attacker is going to get to this system. You’d look at it as a bug on it already, so we know they got it with a Trojan or spyware or a keylogger. Then the next thing that’s going to happen is the victim is going to log onto a server with their credentials, some resource with their credentials. Well, the keylogger can see exactly what they typed in.
You get that information back and then the attacker uses that info to log in also to the same server.
Now, that is a little bit difficult with a domain controller in a Windows network because
the attacker’s computer would have to be part of the network. But, the attacker might be able to gain
control or gain physical access to this computer. There are so many ways to do this if you have spyware, Trojans, or keyloggers. That’s how you can gather passwords. This is the way attackers often gather passwords, is to have one of these three pieces of malware on the system

There’s also the idea of a Pass-the-Hash or PtH attack, often known as a hash injection attack,
and what’s going to happen is this deals with password systems that exchange hashes. What happens is there’s going to be a compromised hash that’s injected into a local session between
somebody and their network. Then the hash is going to be used to gain access to validate network resources, extracting the domain account hash, and eventually login onto the domain controller.
If we look at the steps that happens. Here’s an unsuspecting user, taps on the keyboard and logs in,
the hashes are stored. There is a server, not really a domain controller because
a domain controller would be something that is running Kerberos and Kerberos does not do hash exchanges like this. But, it could be an old-school domain controller like from NT40 or something like that.
Either way, is some type of service that the user is logging into, there are ways of doing this
with domain controllers also. But there has to be certain existing conditions to make it happen.
In fact, with the LLMNR/NBT-NS poisoning that is done on a domain. Either way, the next thing that happens is the attacker is going to use some type of local or remote exploit to compromise the server. Like I was saying, there has to be some other part to it. In this case, there is a compromise of the domain controller, and now what’s going to happen is the attacker is going to extract the domain admin hash. Then they’re going to inject that hash into the session that this user has and then use that to attack the network assets of the domain of this service.

This is a Link-Local Multicast Name resolution is what this is and it uses multicast to help resolve the names of hosts on the network, and NBT-NS is net bios.
That NS is named server, so Net Bios Name Server is when you have a Microsoft system that’s running their old net bios, networking that was created back in the early ’90s, late ’80s, actually early ’90s, and it is extremely vulnerable.
When we’re talking about remediation,we’ll talk about how to not be vulnerable to LLMNR/NBT-NS poisoning. In this case,the first thing that’s going to happen is the attacker is going to have a listener that they install that is looking for people who are logging in.
The user then is going to send like a host name, whack. That’s the saying I want to get to a specific server. The listener is already on there listening for LLMNR/NBT-NS broadcasts.Then when that broadcasts happens, the LLMNR or I could just say the LN poisoning or something like that to make it shorter, poisons it and it sends a dataset were not found to the user.
But literally what happened in the meantime is the attacker was able to accept the NTLMv2 hash of this user. Then they have the hash now of that password. Then what the attacker does is uses a cracking software like John the Ripper to crack that hash and reveal the password and then they can log in to the network later on as this user. The part of the lab that you have to look out for is when you type in the resource and you get an error. I’ve had a lot of students stop there and say, “Oh, this isn’t working, I got an error”. Well, that’s a fake error. That was fake, an error sent by the attacker to capture that information from the use.

In this case, it’s an authentication attack. This is actually used to attack Kerberos and so it’s for authentication systems using Kerberos without providing the user password. What happens is the attacker dumps Kerberos tickets of legitimate accounts. There are these credential dumping tools that you can use, Mimikatz is probably the best tool for this type of attack.
The attacker then launches that pass the ticket attack by stealing the ST/TGT.
That’s a ticket granting ticket from the end-user machine or stealing that ticket granting ticket from a compromised authentic authorization server, which is a Microsoft domain controller.
Then the attacker uses that retrieved ticket to get access to the network services thereafter. Tools like Mimikatz, Rubeus, even Windows Credentials Editor are used for these types of attacks.
This is a pass the ticket. Pass the ticket used to attack the ticket granting ticket capabilities of Kerberos in a Microsoft Windows domain controller environment