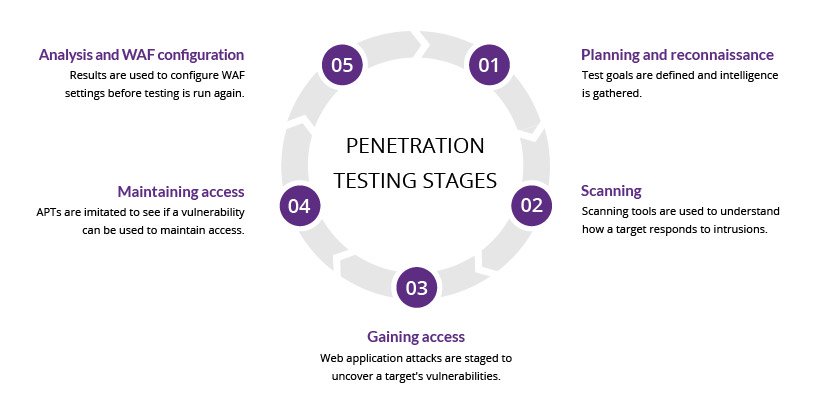
Penetration testing, or pen testing, is a way of testing the areas of weaknesses in systems by using various malicious techniques. A penetration test simulates methods that an attacker would use to gain unauthorized access to a network and compromise the systems and allows an organization to understand how well it would tolerate a real attack.
It’s important to note that pen testing is not the same as vulnerability testing, which only identifies potential problems. Pen testing involves hacking a website, network or server with an organization’s permission to try to gain access to resources using various methods that real-life black hat hackers would use.
One of the primary reasons why an organization would use pen testing is to find and fix vulnerabilities before the cybercriminals do. Penetration testing is a technique used in ethical hacking.
Here are some common levels of penetration testing:
- Black Box Testing:
- Black box testing is conducted with limited or no prior knowledge of the target system. Testers approach the system as an external attacker with no internal access or information.
- White Box Testing:
- White box testing is the opposite of black box testing. Testers have full access to the internal details of the target system, including source code, architecture, and documentation. This type of testing allows for a thorough assessment of the system’s security.
- Gray Box Testing:
- Gray box testing is conducted with partial knowledge of the target system. Testers have some information about the system, such as network diagrams or user credentials, but not full access like in white box testing.
- Internal Testing:
- Internal penetration testing focuses on assessing the security of an organization’s internal network and systems. Testers simulate attacks from within the network to identify vulnerabilities that could be exploited by insiders or attackers who gain internal access.
- External Testing:
- External penetration testing concentrates on evaluating the security of external-facing systems, such as web servers, email servers, and firewalls. Testers attempt to exploit vulnerabilities that could be accessed from the internet.
- Web Application Testing:
- This type of testing specifically targets web applications. Testers attempt to identify vulnerabilities in web applications, such as SQL injection, cross-site scripting (XSS), and authentication issues.
- Wireless Network Testing:
- Wireless penetration testing assesses the security of an organization’s wireless networks, including Wi-Fi networks. Testers look for weaknesses in encryption, authentication, and access controls.
- Social Engineering Testing:
- Social engineering testing focuses on the human element of security. Testers use tactics like phishing, pretexting, and baiting to manipulate employees into revealing sensitive information or taking certain actions.
- Mobile Application Testing:
- Mobile app penetration testing is designed to find security flaws in mobile applications, including Android and iOS apps. Testers evaluate issues such as insecure data storage, insecure communication, and poor authorization.
- Physical Penetration Testing:
- Physical penetration testing involves attempting to gain unauthorized physical access to an organization’s premises. Testers may use techniques like lock picking or tailgating to assess physical security controls.
- Cloud Infrastructure Testing:
- With the increasing adoption of cloud services, this type of testing assesses the security of cloud-based environments and configurations, looking for misconfigurations and vulnerabilities.
- IoT (Internet of Things) Testing:
- IoT penetration testing focuses on identifying vulnerabilities in connected devices and their communication protocols. This helps secure IoT ecosystems.
- Red Team vs. Blue Team Exercises:
- Red teaming involves simulating a full-scale attack on an organization’s infrastructure, while the blue team defends against it. These exercises provide realistic scenarios to assess an organization’s readiness and response capabilities.
Each level of penetration testing serves a specific purpose and can be tailored to the unique needs and security concerns of an organization. The choice of which type of testing to conduct depends on the organization’s goals, the systems in place, and the desired level of security assurance.