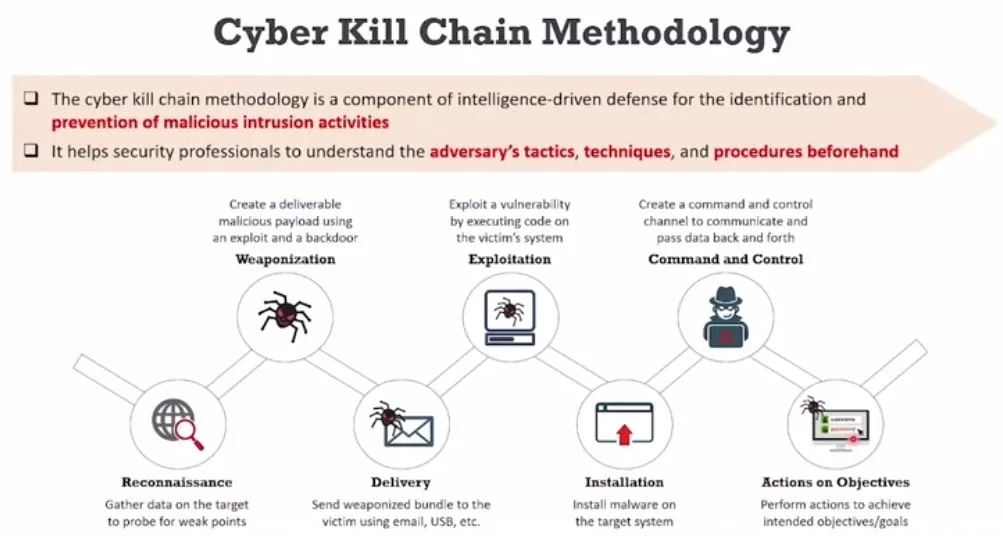
The figure shows the cyber kill chain. It sounds mysterious but actually it’s not that mysterious. We have reconnaissance, weaponization, delivery, exploitation, installation, command, and control and action on objectives. What does all that mean? It’s a chain.
Like a chain, I remember riding bicycles when I was a kid and the chain broke, boom. When that chain breaks, you can no longer move forward. That’s the case here too. If you can break the chain, then the attack no longer happens.
What does that mean? Let’s say that I’m an attacker and I’m like, I’m going to attack that organization and maybe take down one of those employees, and so I do some reconnaissance, and I find out that there are five employees who seem like good targets. I craft an email that has a target that I have weaponized. It is an attachment that when the employee opens it, it’s going to hack their computer system. I weaponize and then I email to the five employees, and it lands on their system.
Employee number 1 sees the email and it says free Starbucks card if you attend this online seminar, just click here and the email looks weird.
Employee number 1 deletes it.
Employee number 2 looks at part of the title, deletes it.
Employee number 3, actually find it intriguing, but then realizes that it’s from outside the organization, and put it into quarantine.
Employee number 4 does the same thing,
but employee number 5, oh, my goodness. Says, wow, this actually looks cool. I think I will click on it and when he does guess what happens, the exploitation starts because the code unloads and finds the PC and begins to run on the CPU, and the memory, and look around to see what’s going on. But then the antivirus software kills it. Boom, it’s gone.
Where could this have been killed before? In this case, we killed it right after, actually we had the beginning of the installation, so this was between exploitation, and installation. Now, for employee number 5, we could have killed it before exploitation, but we didn’t. We could have killed it before delivery by being able to block emails with attachments, but we didn’t we probably in this case could not have killed it at the weaponization phase because that was off of the radar. But the more the earlier in the chain we kill it and in fact, anywhere in the chain that we kill it,
there are times when the software is installing.
There are times when the software is communicating back with the handlers command and control system. Then by the time we get to this last part, where it’s actually achieving its attended goals, exfiltrating data, creating back doors, whatever it is planning on doing, a ransomware or whatever we’re in trouble by this point, it’s doing its action on objectives.
In the example I gave you, you’re fortunate that this organization had good endpoint protection that stopped the installation of this malware. That’s the cyber kill chain, and what it means.