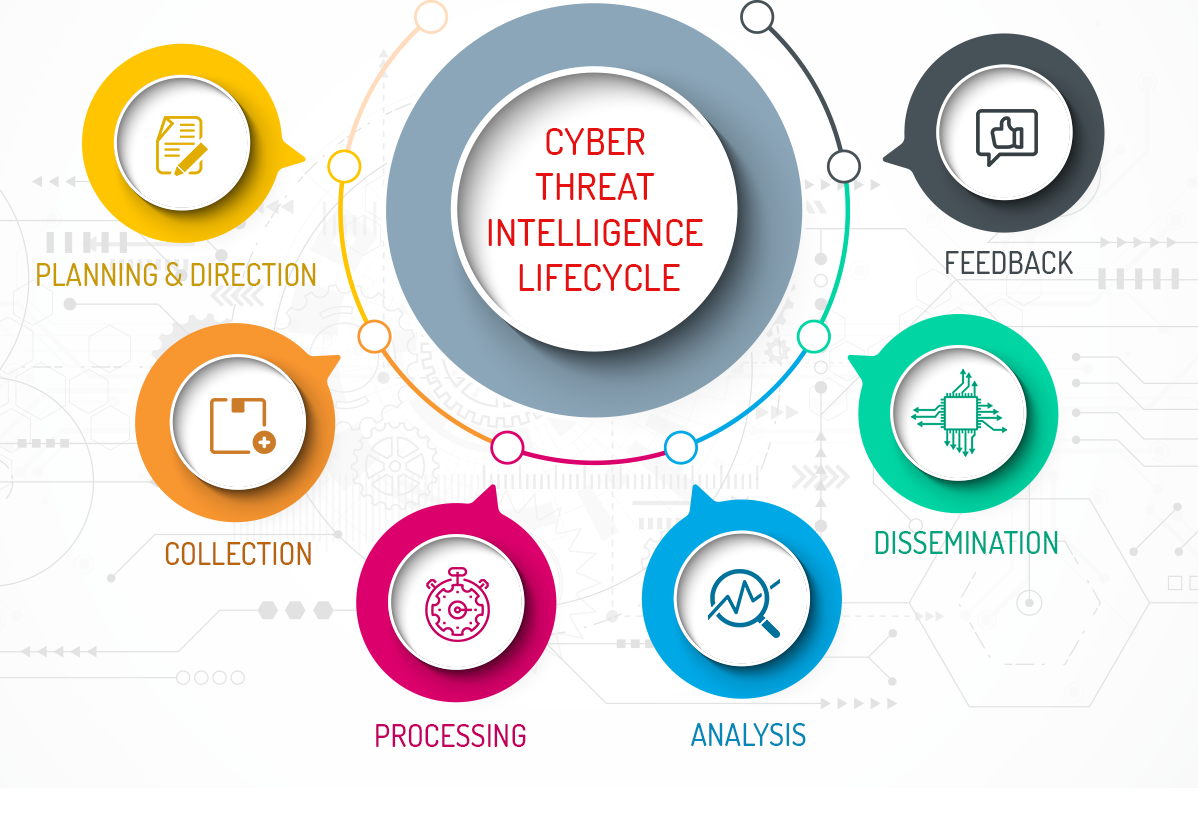
The threat intelligence lifecycle provides the framework for transforming raw security data into actionable, organized intelligence to help inform decisions. There are many intelligence lifecycle versions, but they all share the same objective and core elements. The process guides the cybersecurity team when planning and executing an effective threat intelligence strategy.
Building a threat intelligence strategy can be challenging due to the dynamic nature of cyber threats — organizations must rapidly adapt to the evolving threat landscape. The threat intelligence lifecycle is the framework that helps teams optimize resources and respond to sophisticated threats. It compromises six basic stages, creating a continuous feedback loop.
1. Requirements
This stage provides the roadmap for threat intelligence operations. It is the crucial planning stage when teams agree on the threat intelligence program’s goals and methodologies. They might identify the following elements:
- The attackers — Who they are and what motivates them.
- The attack surface — Which areas are most vulnerable to attack.
- Mitigation and prevention — The specific measures to defend against future attacks.
2. Data Collection
After the security team defines the program’s requirements, it can start collecting the information needed to meet the specified objectives. The team usually searches public data sources, traffic logs, forums, social platforms, and industry specialists.
3. Data Processing
After collecting the raw data, the team must process it into suitable formats for analysis. The processing stage usually involves:
- Arranging the data into spreadsheets.
- Translating data from different formats and sources.
- Decrypting data.
- Assessing the information’s reliability and relevance.
4. Analysis
Once processed, the data is ready for the team to analyze. The analysis should be thorough, addressing the concerns raised during the requirements stage. The security team deciphers the processed data into actionable items and useful recommendations to the relevant stakeholders.
5. Distribution
The distribution stage involves translating the threat intelligence team’s analysis into readable formats to present to lay stakeholders. The way the team presents the analysis differs based on the intended audience—usually, the observations and recommendations should be concise, using plain language (no confusing jargon). The team can distribute the analysis in short documents or slide decks.
6. Feedback
The feedback stage is the end of the threat intelligence lifecycle and often the start of the next cycle. The team incorporates the feedback from stakeholders on the intelligence report — this helps inform the team if the threat intelligence program needs adjustments. The stakeholders might change their priorities, how they want to receive threat intelligence reports, or how often they expect to receive reports.