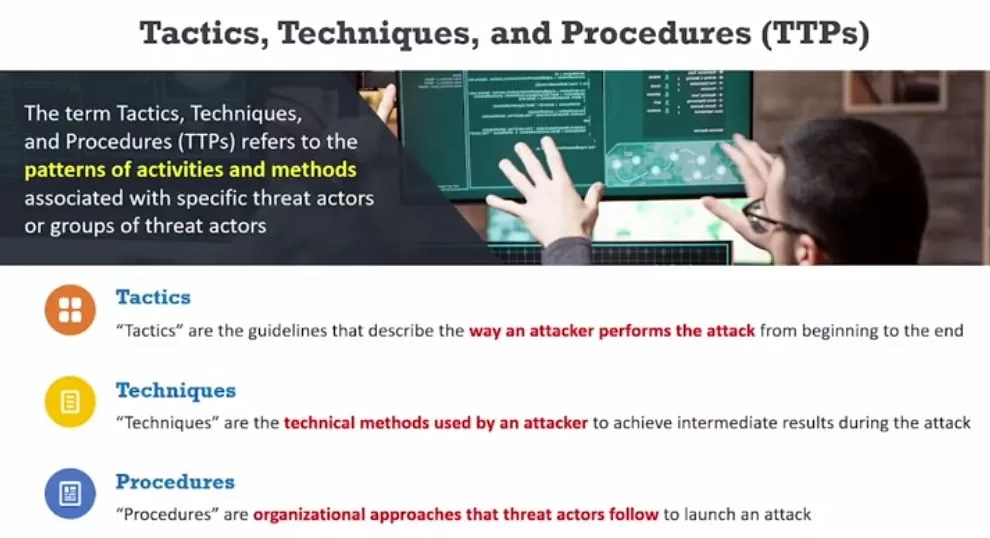
So, you know, everyone has their own style, right? The way they dress the way they walk what they do. And if you know somebody well enough, you’ve you’ve worked with them, you’ve seen their writing the way they express themselves. Let’s say that somebody left a handwritten note on your desk and the the way they said things, the style of the writing and the contents of the note, even though you don’t have a signature who wrote the note, you know exactly who this note is. This was this is jane unequivocally. You don’t even have to think about it. And the reason why is because you’ve established a series of very powerful pieces of information that help you identify that person or identify other people by the way they do things. This is the same thing we do with threat actors. They have ways that are turned into patterns of activities, methods with the way they do things that the tea for tactics is the way they perform the attack. From beginning to end. The T for Techniques is the technical methods, the tools that they use, the procedures are the organizational approach that they take the threat actor to launch the attack. You put these together, it’s almost like getting the thumbprint of the attack. So even though the attacker doesn’t say, hey, I’m with this attacking group, you examine the TTP s and you can tell who they are.

So one of the things that we want to do is look at behaviors in our computing systems or networks that indicate an adversary at work. So let’s go into the fourth floor of a typical office building. And this fourth floor we have customer support customer relations. This is where we have people on the phones all the time. So all of these employees, each one of them have a desktop computer on that desktop computer. They want they run one app. They have regulated break times and lunch times and shifts that people come in whenever one user gets off or finish a shift or goes on break, they log off the application, not the computer, they log off the application and then they take a break and then come back and log back on the application and it’s monitored by supervisors and managers. And that’s all that happens right? These users don’t go into windows and open up a browser. These users don’t download a new app from Microsoft or from anywhere. They just answer the phone. They just take care of the customer data and that’s what they do for a living. That’s how they make their money every two weeks. Now, what happens if one of those computer systems is scanning the network or using power shell of one of those computer systems where there is just people who answer the phone. That’s what they do all day.
But there is a proxy server that Infirm is being sent over this computer or what if one of those employees accounts is using the command line? Using power shell? Maybe not using a web browser but some of their type of http user agent to access resources somewhere else in the company.
Or maybe maybe some user accounts or computer on that floor is a sending information out to a command and control several known feature for attack groups. Or maybe of what do you mean?
What’s going on here?
There’s a D. N. S. Tunnel from one of these workstations. The only thing you can use that for is hiding the fact that you’re sending data out of the organization or a Web Sheller or piling up data different places on the network. Each of these. This is not normal behavior for normal users, normal employees. The these are the behavior of an adversary, somebody has control of an account or of our work station and they’re trying to use that against you. So these are some very important behaviors to look for in a network to identify adversaries