What is information security? While we have information, information is actually
different than data. Information has meaning, and as such it’s more valuable and what we want to do that information is secure it.
Have a little bit of a state of well-being of that information, in that infrastructure with respect to the possibility of theft or tampering or disruption of that information.
So what we want to do is keep the threat of theft, tampering, disruption either low or to a tolerable level and really zero, theft or tampering is even better. So, we want to keep it as low and tolerable as possible. So, the need for security is great.

It’s a huge need for security. One of the reasons is of the evolution of technology. We are evolving technology so quickly that we have let security get away from us in some cases, and that technology is not focused on security. Usually, it’s focused on ease of use, want to make it as easy to use as possible. Also, we rely on computers for everything, accessing, providing, storing information. We have network environments of various types, from on-premise networks to the Cloud, to IoT to OT networks, to wired networks of various types, to wireless networks of various types. Man, quite a lot. Now we look at the impact of security breaches to their corporate, not just corporate, but let’s
say to the organization. Because maybe you’re not a corporation. Maybe you are a family in a house and one of the family members got hit by some type of attack, or maybe you’re a non-profit organization. No matter what you are, we don’t want you to fall prey to security attacks, so that’s why we need
information security so much. Also, we have complexity that increases layer upon layer in infrastructure, in administration, in management of information security systems. That complexity also leads to attack. So we have a need for security.
UNDERSTANDING THE SECURITY ELEMENTS
So let’s look at some of the elements of information security.

The first one we see is the idea of confidentiality. When you see that term,think of encryption. We want to make sure that only authorized people have access to the information then integrity.
When you think of integrity, think of digital certificates or maybe even hashes. What we want to do is make sure that the information has not been changed irrespective of what medium it goes through and who sent it or received it. It hasn’t been changed.
Then we look at authenticity. We want to make sure we know who it is, who has conducted the exchange of information because we want each party to authenticate, we know who they are. Non repudiation. We want to make sure that the sender of the message can’t say I didn’t do it. I never sent that message. They can’t deny having sent it. Why? Because there are identifiers
bound up in the message that are inextricably linked to the sender. So we know that the sender did it and through all of these elements, we want to make sure that the data, the information, the communication is available allowing us to deliver and store and process information as an authorized user. I want to be able to get to, I don’t want to log into open up my resources and make use of them, make sure they’re available. Even though I have encryption and
digital certificates and IP second drive encryption and other security items going on. I still want to have my data available.
THE SECURITY ,FUNCTIONALITY & USABILITY TRIANGLE

In terms of functionality, so I have security, I have all these restrictions, I have log-ins, I
have encryption, etc. But I have also features. I have application developers. They’ll allow me to do all stuff with the software. But in order to use those features is very nice to have usability. Or have a nice graphical user interface and buttons and 3D animations. When I click on a menu, it’s all nice to have around. Which one of these is going to be featured the most?
For instance, if I have security, I may not be able to use the nice functionality of usability or if I have too much usability, maybe I have less security. We’re always kind of bouncing around between these trying to move as closest to security as possible keeping functionality and usability around too. There are security challenges.

Let’s say that you are a corporation and it is the 80s and you’re running your organization just like normal but then a company called Enron implodes taking down billions of dollars. Then Congress and the Senate meet and they pass laws. Now there is a set of laws called Sarbanes-Oxley or SOX. Guess what you have to do, comply. Now you have laws and regulations and let’s say that your organization merges with an organization that works with clinics and hospitals and now you have HIPAA. Then let’s say that you decide to start doing government contracts and now you have FISMA. It goes on and on.
You have laws and regulations that you must comply with. Then we have security challenges like lack of qualified and skilled cybersecurity professionals. Now, I hope right now that you will help us solve this by being one of the qualified and skilled cybersecurity professionals.
Difficulty for centralized insecurity in a distributed computing environment. You have a large
organization like a corporation that has on-premise data centers. They have a connection to
Azure and AWS Cloud providers. They have manufacturing arms that have IoT and OT networks. They have Wi-Fi networks and Bluetooth, and it just gets crazy. Lots of potential
security problems. Distributed all need to be secured. Also, we have a fragmented and complex privacy and data protection regulation industry. Which data protection law or regulation am I under? It’s hard to figure out sometimes and sometimes it even takes a professional and legal help for larger organizations to put that together. Then we have compliance issues because we have people who bring their own devices. We have tablets, we have phones, and so on. We have these policies in the organization, but then we have compliance and we have to make sure
they work together. Then we have relocation of sensitive data from legacy data centers where we each just have them in a file server and then we backed it up onto tape and now it’s in
multiple Cloud structures. What if it’s not configured appropriately to protect that data? Tell you what? There are many different security challenges. It’s usually not just one of these, but a combination of most, if not all, of these security challenges.
Understanding Motives, Goals, and Objectives of Information Security Attacks
Now, what happens is there are entities, people, attackers out there that want to get to your data. And so, they have motives and goals. They have objectives. But, you know what? They can’t attack you unless they have this equation solved, right? So, let’s say that there is a medium sized business and they have a website and the website is used all the time. And helps bring in money, helps direct users to information. But this website has a lot of vulnerabilities in it, right? Why isn’t it attacked? Well maybe nobody knows about it. Maybe no one has tried to scan it, maybe it hasn’t been paid attention to. So, there is no goal or motive to attack the website, even though there are methods to take it down, even though there are vulnerabilities on the website, there is no motive.

All right, so, then again, you can have a company, let’s say you have a company and this company has a website, web application and there’s a group of hackers, attackers, threat actors that hate that company. And so, they’re hacking away and trying but guess what? There’s no vulnerability, there’s no way to get into it. And they’re continually frustrated. That would be nice if we want to stop people from attacking. So, it’s all three of these that you need to be able to have an attack. So the motive originates out of the notion that the target system stores or processes or contains something valuable. And so the attackers want to have at it. So those attackers want to exploit the vulnerabilities in the system. And, what are the motives? Are they just might want to break that business? Are they might steal information? They might want to create fear and chaos. I’m just getting chaos, disrupting the critical infrastructures. They may want to steal money, financial loss. They might want to damage the rep of the target and make them look bad, yeah, this company is bad. So many different things that they might want to do.
Classification of Attacks

Let’s look at attacks. There are several different types of attacks in terms of classification.
A passive attack, they’re just looking around. For instance, let’s say that they’re watching, they’re sitting. Let’s say there’s someone in a parking lot. They have a laptop and they’re looking at the Wi-Fi traffic, just sniffing it, looking at what traffic happens. They’re not causing anything to happen. It’s just passively listening. Or maybe somebody in one building has a parabolic antenna. They’re looking at the vibrations of the window in the conference room of the building across the way and listening in on the meeting in a conference room. That’s passive. They’re not actively interacting. Or they’re going to LinkedIn and reading information about employees or about the company, or they’re going to a job site looking for jobs that are being advertised to see what types of protocols and programs that company has that they’re hiring employees to help with. Those are all passive. There’s no interaction. It’s passive.
An active attack is when you tamper with, you change things, you interact with, or you may even disrupt communications by conducting an attack like a man-in-the-middle, session hijacking or SQL injection. An active attack is also if instead of just parking outside of the organization with a listening device, you just go into the front desk and you asked for information. You have now gone active. You’re interacting with the target of your attack.
A close-in attack is when there is close physical proximity. For instance, people have been attacked from across the world quite a lot. But what if they’re in the building next door? Or what if the person is dressed like a delivery person, but really they’re an attacker inside the organization with access to systems now where they can plug in stuff, and gather, and disrupt an access to things. So for instance, a close-in attack can be social engineering or eavesdropping right there inside the organization. Or maybe standing there looking casual but really shoulder surfing, reading what somebody is typing or writing, or maybe somebody throws away an important document that somebody takes it out of the trash and uses it in an attack.

We also have insider attacks. This is when somebody who works for the company violates the rules, intentionally causing damage, destruction to the organization, like for instance, stealing a physical device. They may steal a laptop or a tablet or something like that, and that device might have information on it that can damage the organization if it gets out of the organization. Or they may stay a little bit late and that they’d working late and then making sure everyone’s gone off the floor, go in their pocket and pull out a little key logger. You have you seen these before? Watch. Try this, open up a tab in your browser right now and in DuckDuckGo or in Google, type in key logger. See this word I have here and type it in? Key logger, and then go to shopping. If you go to shopping, you’ll see the key logger is a little USB dongle. If somebody’s staying late, let’s say they spent 200 bucks, bought three, or four, or five of the key loggers, they can find the attack target. Let’s say they go plant one behind the PC of the supervisor, go plant one behind the PC of the financial person, etc. Then they can collect the data. Or they can have a flash drive and plant a backdoor, malware, all kinds of stuff, right? These are insider attacks.
Then we have distribution attacks. They tamper with hardware or software before it even makes it to the site. So like for instance, I’ve worked for many organizations in the IT department where we had agreements with supplier that when we got PCs or servers delivered, they would have them pre-configured for us with our own images on them. That would save a lot of time. What can happen with the distribution attack is somebody can interfere at that at one of those companies. When we get the PC, it’s compromised. These are very similar, but it’s a little bit different to supply chain attacks where something like that happens with the distribution of software.
For instance, you have a Ubuntu Linux box and you’re doing an update, but little do you know somebody has changed the update parameters so that there is a malicious update that’s coming in from an official source. That could be like a supply chain attack. Distribution attack, supply chain attack. There are all kinds of attacks that can happen to organizations.
Information Security Attack Vectors
What are the attack vectors?

We have Cloud computing threats. For instance, we have all these wonderful on-demand services that we can get from Cloud providers. But there’s a possibility of sensitive data leakage. We could have flaws in the way that the application works. There are many different ways that the Cloud communication can be tampered with. They are the idea of advanced persistent threats.
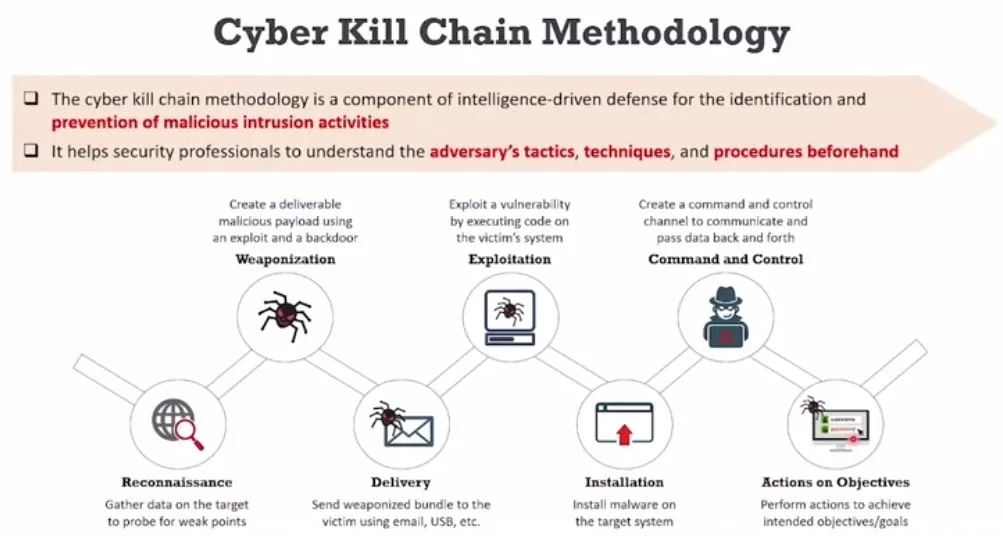
Consider an analyst been called to do some consulting for an organization that they were doing real estate property management for commercial real estate. The problem was though, that there was an email that was sent out to all of their clients that said, for your convenience, we have made it better for you to pay your lease. Remember, this is commercial real estate. If you’re leasing or renting a house for your family, it might be $2,000, $1,000 a month, but if you have commercial real estate, it could be $10,000, $50,000 on up a month for the commercial real estate and we have a new way for you to pay. All you have to do is click on this link or use this ACH number, and you can conveniently pay for your lease. If you or their clients actually did that but somebody said, “Excuse me, why are you changing the way we pay?” The people at the company said, “We didn’t change the way you pay.” They send him a sample of the email. The email was sent officially from that company on their official email. What had happened was somebody had attacked the network. They had stayed there inside the network, full access, and figured out a way where they could steal money. That wasn’t an advanced persistent threat. Do you know what the average amount of time that it takes for an organization to figure out that they’ve been attacked and have an attacker inside their network hacking away at stuff? Do you know the average amount of time it is? What do you think? It is 208 days. That’s the better part of a year.
There’s somebody who could be camped out in your network attacking it. That’s an APT, we have worms and viruses. Big difference between a worm, and a virus. Now, both of them are sophisticated codes that are able to infect. But just like in biology, a virus needs a vector. If somebody has a disease and their hand is sweaty and covered with the disease and I shake their hand, do I now have the disease? No. Actually, there might be a billion viruses on my hand, but I don’t have the disease. They’re not going to crawl up my arm. In fact, if I quickly go wash my hands, the viruses are gone. But, if I shake somebody’s hand and then it feels really clammy and weird and like, oh man, I think that dude is sick and I start eating my potato chips and I transfer the virus from my hand to the potato chip, from the potato chip into my mouth. Well then I’m in big trouble. Viruses need a transport in biology and in technology.
But worms, let’s say that you’re in the garden growing a nice big garden in the backyard, and it’s a summer morning and you dig up a big chunk of the garden and then you get a phone call and you’re talking on the phone and meanwhile, guess what a worm comes out, and it just starts crawling on its own. Worms don’t need transport. They’ll transport themselves. In the world of computers, a virus might need your email application in order to send itself. If you don’t have an email application, it might not even work. The virus may not be able to do anything else, but it can send itself using your email application. The email application is the viral vector.
However, a worm, let’s say I have a laptop, I take it to a network, the worm says, “Hey, cool. A network,” and a worm crawls out of my laptop and starts finding all kinds of other ports that are open and other devices that are connected to the network and spreads itself. No need for a vector. Big diff between worms and viruses. Keep that in mind. Just match it up to biology. You’ll be fine.
Ransomware. Have you ever heard of ransomware? . If you’ve watched any news, if you work for any organization, you’ve heard of ransomware where a screen pops up, it’s a splash screen on your computer and it says, all your files have been locked. If you want to unlock your files, send us five Bitcoins before 11:30 AM tomorrow or 48 hours or whatever. Locking all the files in some threat actors will actually not only lock all the files of a big organization, but they’ll just even take it all, all the data they can get, gigabytes of data and they’ll say, if you don’t pay us, then we will drop this data on the Internet for anyone to see. Ransomware can be pretty bad.
Then we also have mobile threats. A lot of us think our phones are safe. Why? Because the phone hasn’t ever been attacked that we know of before and you don’t see a lot of information about phones, mobile devices, tablets being attacked in the news. But for those of us who deal with cybersecurity, we know that phones, mobile devices, are a definite vector for attack. what I tell all my clients and other people is, where’s my phone? Here’s my phone right here, you need antivirus on your phone.

Other vectors, botnet, specifically for IoTs and mobile phones, they can become botnets where they become the source of the attack and they’re controlled by a controller. Insider attacks, where somebody who’s trusted, who works for the organization, or a consultant, or somebody who’s on the inside attacks the network. Phishing where an email or a text or some other type of communication that looks legitimate and appeals to the person is actually an attack, trying to acquire information. Web application threats, where you are trying to just get to a website, download it, you’re trying to download a web app and use it, but you get attacked, something happens and they try to redirect you or steal information or get you to click on a link that will become a threat or IoT. You have devices, Internet of Thing based devices that are compromisable, and they become a threat to the organization because of flaws and these devices that allow the attacker to remotely perform attacks based on that device.
Various Information Security Laws and Regulations
Right, let’s have a look at some laws and regs for information security. Now, if you work for an organization that uses and processes, makes use of customer credit card data, then you are covered by PCI DSS.

PCI DSS is the payment card industry security data standard. And so this is very important for people like I said, processing credit cards debit cards, some of those like prepaid gift cards that you can get and e purses ATM’s, point of sale registers and so on and so applies to all the entities involved with that. And at a high level overview for PCI DSS, what they want us to do is to build to maintain a secure network, protect that cardholder data. We don’t want the card exposed a maintain, a vulnerability management program, implement access controls, regularly monitor the network, regularly test the network, maintain information security policy. So if you don’t do this and you have customer payment data then you can get fined. You can get your privileges of processing credit card data removed and revoked and get very hard to get it back again. So it’s very important to comply with PCI DSS. If you are processing customer credit cards, debit cards etcetera.

The next one is ISO/IEC 27,001. 27,001 actually covers quite a lot. There are a lot of sub topics in 27,001 but there is specifically 27,001:2013 which is the requirements for establishing, implementing, maintaining and continually improving your information security management system. This is actually pretty cool. So if you are interested in doing that, which I think a lot of us are, what you do is you take all of the tenants of 27001:2013. And you match them up with how you are doing in your organization and see if you can bring your level of efficacy, how well you’re doing to the level of 27001:2013 or maybe you’re actually doing things better. But either way, you can look at the way your organization does security objectives and requirements. Information security management, cost effectively managed security risks. Looking at the management status of your information security activities, making sure you’re in compliance laws or regs. Making sure that you have business established information security implemented really well. Making sure that you have good information security management processes, making sure that you have relevant information about security that you get it out to your customers. All of this is part of 27001:2013.
All right, so let’s say that you are an organization and maybe you are a medical clinic, maybe you are a hospital, maybe you deal with surgical instruments, maybe you deal with medical supplies, whatever it is. If you deal with patient data at all in the medical industry, you are going to be subject to HIPAA.

.HIPAA is the health insurance portability and accountability act. That primary purpose is to protect patient data. So some of the simplification of HIPAA rules. We want each provider who does business electronically to use the same health care codes, transaction identifiers. Right? So we want to be able to match code for code, identifier for identifier. So we know who’s talking what. So very important. Also we want to have protection for the personal health information, right? If if somebody is undergoing tests for cancer or some other disease and it’s in the medical record, even if it turns out negative, it might negatively affect that person’s future if that data leaks out. And so it gives the patients an array of rights to not disclose health information.
And then we have a specification for administrative and physical and technical standards for confidentiality, integrity and availability of that electronically protected health data. So we want to protect it, secure it but make it available to those who are authorized to see it. If your health care provider, health plan or an employer dealing with health care, then you want to have again national numbers. These are going to be things like Social Security and other types of national number to identify transactions. Right? So then providing standards, enforcing administration and simplification of rules. So all of this is a very highly simplified kind of distill mint of some of the important stipulations, I guess. We could say HIPAA.